At 8:58pm last night, French luxury skincare group Clarins notified Australian customers of a data breach allegedly tied to ransomware group Everest. But there are questions related to the length of time it took between the company identifying the breach and when customers were advised.
The email confirmed that contact details of some clients had been “illicitly downloaded by a third party” but stressed that no financial information or passwords were compromised.
“You are receiving this message because you may be one of the clients concerned,” the company wrote, before advising customers to remain alert to suspicious emails, calls or texts.
The note also assured recipients that Clarins would “never ask you for your credit card number or your password by email, phone, or text message.”
The email follows three days after Cybernews first reported the breach on 15 September.

The Clarins hack email sent out to Australian customers
Company response raises questions
When contacted by Mediaweek, Clarins Australia confirmed it had been “notified just recently that a third party has illicitly accessed and downloaded files containing contact details of some of our clients,” and said its technical team “acted immediately to resolve the issue, and the incident has been fully contained.”
The company reiterated that “no financial data (such as bank account or credit card numbers or passwords) have been affected” and that relevant authorities had been informed.
When pressed on when exactly the breach was first detected, and how long it took for customers to be notified, a Clarins’ spokesperson maintained that “we were aware of this incident just recently and customers were informed promptly.”
Again, Mediaweek pressed the company on definitive figures given ‘promptly’ is vague and not measurable.
The company, however, remained steadfast in its response, or lack thereof: “For confidentiality reasons, we are unable to comment on this matter.”
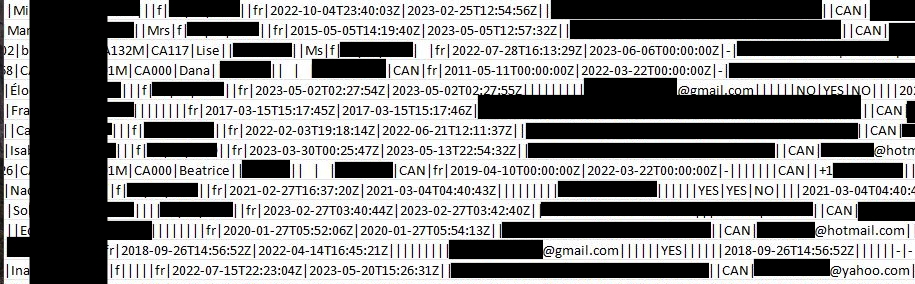
Sample of the allegedly stolen details. Image by Cybernews.
Under Australian law, companies with turnover above $3 million must notify both the Office of the Australian Information Commissioner (OAIC) and affected customers of any breach “likely to result in serious harm” within 72 hours of becoming aware of it, under the Privacy Act 1988 (Cth) and the Privacy Amendment (Notifiable Data Breaches) Act 2017.
As mentioned above, Clarins has so far declined to provide a timeline of when it first discovered the incident. What is clear is that Cybernews only reported on the breach after spotting Everest’s claims on the dark web – meaning the hack itself may have occurred well before.
And, given the company’s scale, it is reasonable to expect that even if the company was unaware of the breach itself, it would have been made aware of reporting from sites like Cybernews through media monitoring services, such as Meltwater, which are designed to alert companies to media activity.
The Everest gang
The Everest ransomware cartel, believed to be Russia-linked, claimed responsibility for the Clarins attack, posting samples of customer data on its dark web blog. Screenshots appeared to include names, addresses, dates of birth, email addresses and purchase histories from Clarins’ regional online stores.
Everest has previously claimed attacks on AT&T, Allegis Group, Coca-Cola’s Middle East division and US retailer Crumbl Cookies. According to Cybernews’ Ransomlooker tool, the group has victimised over 100 organisations in the past year.
